Most of us don’t think we have anything worth hacking, and as a result don’t keep tabs on our own internet safety. However, by not keeping up to date with your own online security this will not only put yourself at risk, it puts others at risk too. In this post we’re going to look at internet safety and some tips on how you can make sure you’re secure. As one of my favourite school teachers once said, “there’s no such thing as a silly question”, so I’ve tried to answer some of the most ‘obvious’ questions surrounding this topic. Don’t feel like a noob when it come’s to internet security. This is something that’s always being updated and it doesn’t hurt to stay up to date with the latest security trends. For those that are still new to the concept of internet safety, I’ve included a glossary to make this a little easier to understand.
Glossary
It’s time to put on those spectacles and brush up on your tech vocab.
Anti-virus Software
Anti-virus software is a programme or set of programmes designed to detect and destroy computer viruses.
Browser
A browser is a programme that provides a way for users to access the internet and view pages on your computer, such as Google.
Cookie
Cookies are small files sent from a website and stored on your computer by the web browser, while you are browsing the internet. They are designed to record specific data, about a particular client and website.
Cyberbully
A cyberbully is someone who uses an online platform to hurt, persecute or intimidate another person.
Hacker
A hacker is a person who uses computers to gain unauthorised access to data.
Identity Theft
Identity theft is the fraudulent practice of using another person’s name and personal information, often for financial gain.
Phishing
Phishing is the fraudulent practice of sending emails pretending to be from reputable companies in order to get individuals to reveal their personal information, such as passwords and credit card numbers.
Virus
A virus is a piece of code which is capable of copying itself and typically has a detrimental effect, such as corrupting a computer’s files or destroying data.
What is the meaning of Internet safety?
According to We Are Social, more than half of the world’s population now uses the internet. “It’s only been 25 years since Tim Berners-Lee made the ‘World Wide Web’ available to the public, but in that time, the internet has already become an integral part of everyday life for most of the world’s population.”
Digital in 2017 Global Overview from We Are Social Singapore.
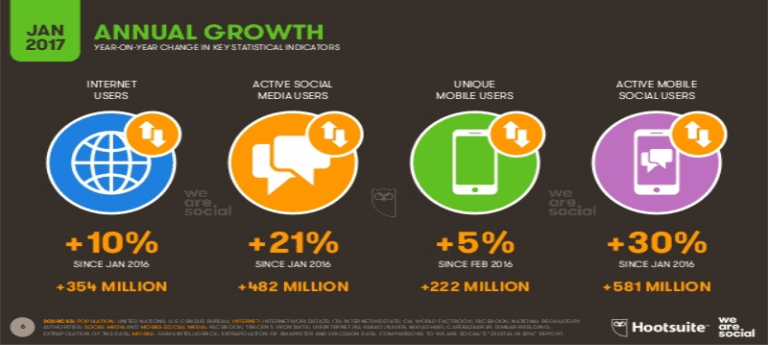
As you can see from the above infographic, the amount of internet users, active social media users, unique mobile users, and active mobile social users has only increased. This means that more and more people are using the internet, and in different ways. The internet has changed the world, bringing people together and allowing technology to develop at an exponential rate. If I were to try and list all the examples of positive impact that the internet has had on the world, we would be here till next year.
However, as in the famous words of Uncle Ben from Spiderman, “With great power, comes great responsibility”. Internet safety, or online safety, is being aware of your personal safety against security risks associated with using the internet. As the amount of internet users increases, and the internet becomes inherently part of our daily lives, so we put ourselves at risk. With an increase in the number of internet users, so the number of cyber threats and hackers increases too. In todays digital society, some of the most effective bank robbers are armed with computers, not guns. This has since developed into a world where it’s been estimated that half of UK’s SMBs could be hacked in under an hour.
ITonlinelearning Safety Tip:
In order to ensure your safety when browsing online, you can install the following on your PC or mobile for general online safety:
Antivirus Software
Check out Kaspersky for the latest antivirus software. By downloading this programme you can keep your mobile device or PC virus free with constant updates to make sure you’re always protected.
VPN
Use a VPN to maintain online privacy when browsing. By downloading a Virtual Private Network (VPN), you add an extra layer of security to your online browsing by hiding your IP address and location.
Password Security
Download a password manager to safely store and manage all your passwords.
What is Spam Email?
Spam email, also known as junk mail, is any unsolicited messages sent through email, usually in the form of commercial advertising. It’s a way of flooding the internet with the same message with the hope of commercial gain. If you’re a fellow Ted Talk fan such as myself, check out James Veitchs humorous approach to spam email and how he’s combating the problem.
James Veitch and Spam Email
One of the biggest problems associated with spam email is that it’s often sent with the intent to spread a virus. The biggest threat is when virus makers and spammers combine their efforts. This often results in viruses being sent on a massive scale and can cause major damage. They do this by sending viruses in the form of online links which can be found within an email, sometimes even using clickbait. Clickbait can come in different forms, but it can often come in the form of an eye catching link with an interesting or shocking heading that urges you to click on it. This clicking action eventually results in the hacker gaining access to your data and can cause serious damage. Click bait often looks something like the image below, and can sometimes be found in spam email.

Many people across the globe have also fallen victim to forgery by spammers. This happens when spammers use software to pretend to be someone they’re not. They hijack people’s addresses which enables them to conceal the true origin of the messages. What this means is that spammers use technology to access your email inbox, social media app or other forms of communicating online, and pretend to be you (or someone else) in order to gain information. The reason is often centred on gaining access to private information, which enables them to access all different kinds of information, which is often used for financial gain. According to runbox.com, “at the present more than 95% of email messages sent worldwide is believed to be spam, making spam fighting tools increasingly important to all users of email.”
ITonlinelearning Safety Tip:
In order to prevent spam email from finding it’s way to your inbox, you can do the following:
Where possible, try not give out your personal email address
We suggest keeping two email addresses, one for personal information and one for online accounts that may receive spam mail. A nifty website to keep in mind is called Bugmenot.com which is an internet service that provides usernames and passwords to let internet users bypass mandatory free registration on websites.
If you feel it could be mail with malicious intent, then it should be reported
To report spam email, you can forward unwanted or deceptive messages to the Federal Trade Commission at [email protected]. Be sure to include the complete spam email.
Use an email filter
If you have a Gmail account, you can create rules to filter your emails. You can manage your incoming mail using Gmail’s filters to send email to a label, or archive, delete, star, or automatically forward your mail.
Do not give out personal information over email
Unless you can trust the source, giving out personal information over email is a big no-no. Always check the sender is from reliable source.
Spelling errors are often a good indication of spam
Organisations hire people to proof read any information that is sent to the public. Bad spelling is a sure warning sign of a suspicious looking email.
Don’t open suspicious looking email attachments
Hackers often hide viruses in the form of attachments. If the attachment is not from a reliable source, do not open it.
Don’t make purchases based on on suspicious looking emails
If you get an email about a brand new iPad for sale that costs only £20, and you’re thinking that’s too good to be true, then it probably is.
How Can You Protect Your Child Online?
We are all pretty aware of the fact that most ten year olds today are probably more tech savvy than you are. When it comes to family gatherings, the older generation are known for using the kids as free tech support. However, children are not always the best evaluators of risk. As we mentioned earlier, online safety is your responsibility, and that also means that you’re responsible for your childs online safety too.

Unfortunately there are many internet dangers out there for kids. From exposure to sexual predators to cyberbullying, children are always at risk when it comes to online activity. Cyberbullying is bullying that occurs online via social media sites, chat rooms, e-mails, gaming sites, or through text messaging and phone calls on smartphones. Cyberbullying is one of the biggest problems facing kids today. According to BullyingUK, 43.5% of children surveyed between the ages of 11 and 16 were bullied on social sites. That’s almost 1 in 2 children in the UK that are bullied via online platforms.
ITonlinelearning Safety Tip:
In order to protect your child online, you can do the following:
Talk to your kids about cyberbullying
A good place to start is with a resource available through Norton, which gives great advice for talking to your kids about cyberbullying.
Recognise the signs of cyberbullying
If you would like to find out about the warning signs of cyberbullying check out NOBullying.com for more information.
Report cyberbullying
If you want to help combat cyberbullying, you can report incidents to social media sites, internet service providers or website administrators.
Set limits with “Restricted mode” options
Click here to find out how you can enable restricted mode for your familys Youtube account to protect your kids from inappropriate content.
Set a good example by teaching your kids about online netiquette and how you treat others online
The best leaders are those who lead by example. Teach your kids about online netiquette and how to treat others online. If we can pass on the message of refraining from online abuse, we may create a safer online world for kids.
Secure their gaming systems
Many games today are available online and include live chat rooms. Make sure your child is engaging in a safe space and isn’t being exposed to any inappropriate content.
Teach them not to respond to strangers
Just like when we were growing up, we were told not to talk to strangers, the same applies to talking to strangers online. Children are easily influenced, and talking to the wrong people may be detrimental for their safety.
How Safe is Social Media?
According to the Deloitte Global Mobile Consumer Survey of 2016, they found that 61% of people check their phones 5 minutes after waking up. It was found that social media and messaging apps are some of the first things that people check in the morning, before they do anything else.
Social media is inherently part of most peoples lives. Social media brings people together, sometimes even in the most unexpected ways. Tropical Storm Harvey is one example of how social media was used to bring people together to save lives. With Facebook now giving users the option to check in as “safe” in natural disasters, this has changed the way we seek help, and as a result how we help others.

“..as a powerful storm hovered over America’s fourth-largest metropolis — social media allowed many Houstonians to take their fate into their own hands. Using social media, flood victims who still had power were able to communicate with public officials directly or to bypass them entirely and coordinate their own rescues with private citizens.” The Washington Post
However, as we see how social media can be used to save lives, it can also be used to destroy. As social media plays a more significant role in our lives, it also puts us all at risk for security threats. Using social media comes with more risks than we think. Some of these risks involve becoming a target for cyber criminals.
The risks involved with social media can include having your identity stolen, getting your computer or social profile hacked or letting burglars know your whereabouts. Many people also believe that they don’t have anything worth hacking, so they are not concerned about security in terms of their social media accounts. However, when you neglect security, you not only put yourself at risk, you put others at risk too. This is because once someone gains access to your profile, they might be able to gain access to your friends’ or family’s profiles too.
We often think that cyber criminals use some form of complicated software to hack in to our accounts. In most cases, it’s a lot simpler than that. Hackers often employ what’s called social engineering, which is used in 66% of all attacks by hackers. Social engineering is the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes. This means that hackers are able to access your accounts, or accounts of those within your social network, by accessing your personal information available through your social media accounts.
ITonlinelearning Safety Tip
In order to secure your social media accounts, there are a few things you should consider.
Don’t link social media accounts, if one site is hacked then all your accounts are compromised
If you would like to unlink a social media account such as Instagram from other accounts, follow this link to find out how.
Check your social media privacy settings
Make sure you are aware of what people can and cannot see. Check out Facebook’s Privacy Settings to make sure your Facebook account is secure.
Be aware about phishing schemes and fake friend requests
If you have been approached with a suspicious scheme or have received a fake friend request (from a fake account), make sure to report this by following this link.
Be wary of publishing any identifying information about yourself
This includes posting about holiday dates, as the modern burglar may be more tech savvy than you realise.
Once things are on the internet, it’s almost impossible not to remove it. Consider this before posting anything
Before you post anything, consider the effects this could have on you in the long run. Don’t ruin your chances of becoming president one day with a dodgy college party pic #oops.
Keep in mind that many companies check social media sites before hiring future employees
Many organisations screen future employees before they even get to the interview. Make sure you have an acceptable profile that won’t ruin your chances of employment P.S. don’t worry about all the cat pics, we say they can stay (wink).
How do I keep my computer/phone safe and secure?
Many of us may be up to date when it comes to keeping our computers secure with anti-virus software. But what about our smartphones? We use our phones for shopping, socialising, browsing, banking and more. For ease of access, most of us probably don’t even log out of all the accounts that we use. However these devices contain almost all of our personal information.
One of the most sophisticated smartphone attacks was due to spy software called Pegasus. Pegasus is the name of a spyware that can be installed on devices running certain versions of iOS, Apple’s mobile operating system. According to Wikipedia, upon clicking on a malicious link, Pegasus silently enables a jailbreak on the device and can read text messages, track calls, collect passwords, trace the phone location, as well as gather information from apps including (but not limited to) iMessage, Gmail, Viber, Facebook, WhatsApp, Telegram, and Skype.
In order to keep your computer or phone secure, you need to be aware of what puts these devices at risk. Ignorance is not always bliss. Once you’re aware of the dangers out there, you can actively work against what puts you at risk. Some examples of what may put your computer at risk include:
- Not updating your antivirus software
- Neglecting to back up your data
- Staying logged in to various sites
- Downloading from sites that are not trusted
ITonlinelearning Safety Tip
To keep your phone or computer safe from any attacks, make sure you consider these security suggestions.
Back up your data
Backing up your devices to cloud technologies is the most efficient way to prevent your data from being lost. If you own an Apple Device, you can back up to iCloud.
Switch off a wireless connection when it’s not in use
It’s often tempting to link to free wireless hotspots, however this is how you put yourself at risk from hackers attacking your device. Make sure that when your not at home, or within range of a wireless network that you trust , switch off your devices Wifi connectivity.
Place tape over your webcam, even Mark Zuckerberg (CEO of Facebook) does it
According to the FBI, this is something everyone should do for an extra layer of security. This will prevent hackers from spying on you while you use your laptop or PC.
Set your devices default Bluetooth configuration to “non-discoverable” mode by default
Believe it or not, but hackers can even access your device via bluetooth. Make sure your bluetooth is switched off when you’re not using it to prevent any security breaches.
Be cautious when downloading applications that could contain malware
If you’re going to download an application for your device, make sure it’s from a recognised source like Apple’s App store or Google’s Play store.
Conclusion
Internet safety is a topic that is often talked about, but many of us overlook its importance. If you’re a beginner, it can be difficult to get through all the tech jargon and find valuable information pertaining to your needs. Hopefully after reading this, you will be a little less of a beginner when it comes to internet safety. For those that have an interest in online safety as a career, but have maybe only just started out in the IT industry, you can check out our New to IT Security course bundle. This bundle has no prerequisites and is perfect for those who wish to start their career in security.
What tips do you think are important for beginners who are interested in online safety?